
The Office for Civil Rights (OCR) is responsible for issuing periodic guidance on the provisions in the HIPAA Security Rule. (45 C.F.R. §§ 164.302 – 318.)
The guidance for conducting a risk analysis that meets the requirements of the HIPAA Security Rule has nine very specific elements that must be included.
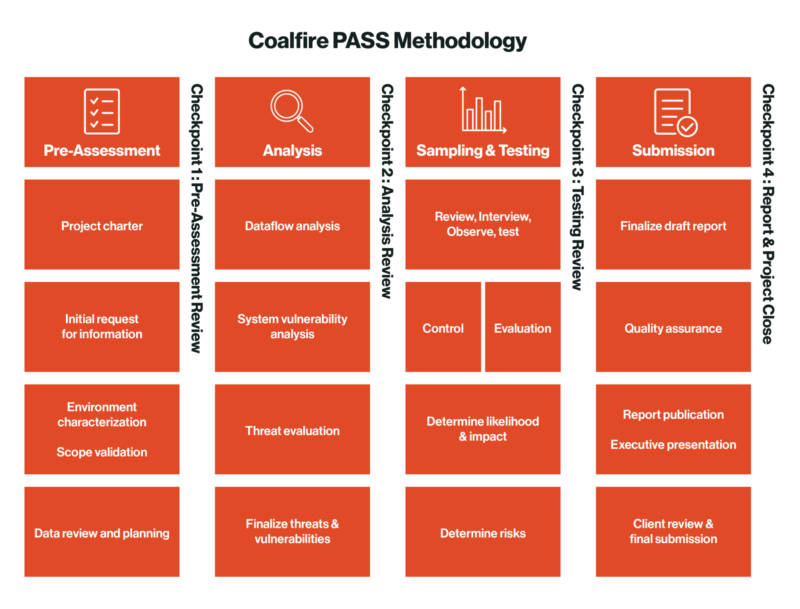
Coalfire’s PASS (Pre-Assessment, Analysis, Sampling and Testing, Submission) Methodology, aligned with NIST Special Publications, ensures that all nine are addressed.
Step 1
OCR Guidance
Scope of the Analysis
- The scope of risk analysis that the Security Rule encompasses includes the potential risks and vulnerabilities to the confidentiality, availability and integrity of all electronic protected health information e-PHI that an organization creates, receives, maintains, or transmits.
Coalfire PASS
Environment Characterization & Scope Evaluation
- From the initial scoping call through the sales process and the Service Order we document what is in scope for the RA assignment.
- RFI-1 provides us with client supplied data flows and network diagrams to help characterize the environment and validate the scope.
Step 2
OCR Guidance
Data Collection
- An organization must identify where the e-PHI is stored, received, maintained or transmitted.
Coalfire PASS
Data Review and Planning
- Information gathered in RFI-1 and RFI-2 provides Coalfire with known PHI assets such as applications, data centers, transmission protocols, etc.
- Any new PHI assets discovered during analysis and interviews will be confirmed during RFI-3
Step 3
OCR Guidance
Identify and Document Potential Threats and Vulnerabilities
- Organizations must identify and document reasonably anticipated threats to e-PHI.
Coalfire PASS
Evaluate/Finalize Threats & Vulnerabilities
- Based on the environment characterization of PHI assets and dataflow analysis, Coalfire compiles the threats and vulnerabilities to be analyzed.
Step 4
OCR Guidance
Assess Current Security Measures
- Organizations should assess and document the security measures an entity uses to safeguard e-PHI, whether security measures required by the Security Rule are already in place, and if current security measures are configured and used properly.
Coalfire PASS
Control Evaluation & Testing
Coalfire uses the RIOT method to assess if controls are in place and effective:
- Review (policies and procedures)
- Interview (key stakeholders and SMEs)
- Observe (security & privacy walk-through)
- Test (examples of control outputs and effectiveness)
Depending on client requirements, control test plans can be built using NIST 800-53, NIST CSF, or any client requested framework.
Step 5
OCR Guidance
Determine the Likelihood of Threat Occurrence
- The Security Rule requires organizations to take into account the probability of potential risks to e-PHI.
Coalfire PASS
Determine: Likelihood
- Coalfire uses NIST guidance to determine likelihood based on:
- Historical record
- Threat motivation
- Vulnerability nature
Step 6
OCR Guidance
Determine the Potential Impact of Threat Occurrence
- The Rule also requires consideration of the “criticality,” or impact, of potential risks to confidentiality, integrity, and availability of e-PHI.
Coalfire PASS
Determine: Impact
- Coalfire uses NIST guidance to determine impact of risk to CIA of PHI for the following factors:
- Operational
- Human
- Financial
- Reputation
- Patient Harm
- Client Relationship
- Legal/Regulatory
Step 7
OCR Guidance
Determine the Level of Risk
- Organizations should assign risk levels for all threat and vulnerability combinations identified during the risk analysis.
Coalfire PASS
Determine: Risk
- Coalfire uses NIST guidance to determine level of risk for each T/V pair based on a 5x5 matrix mapping likelihood and impact.
- Coalfire provides the client with recommendations on the risk tolerance threshold (baseline is “High”)
Step 8
OCR Guidance
Finalize Documentation
- The Security Rule requires the risk analysis to be documented but does not require a specific format.
Coalfire PASS
Submission Phase
- Final drafts are submitted for the client to review for any errors or omissions.
- Final report is issued, including:
- An executive level presentation of significant findings.
- An executive summary report.
- A comprehensive workbook of threats, vulnerabilities, risk ratings, findings, and recommendations.
Step 9
OCR Guidance
Periodic Review and Updates to the Risk Assessment
- The risk analysis process should be ongoing. In order for an entity to update and document its security measures “as needed,” which the Rule requires, it should conduct continuous risk analysis to identify when updates are needed.
Coalfire PASS
Risk Management and Review
- Coalfire offers advisory services to create a partnership with clients during remediation and mitigation efforts.
- Long term client relationships include periodic evaluation of controls, scheduled risk analysis, and vulnerability assessments such as penetration testing and social engineering.
Summary
- Risk analysis is the first step in an organization’s Security Rule compliance efforts. Risk analysis is an ongoing process that should provide the organization with a detailed understanding of the risks to the confidentiality, integrity, and availability of e-PHI.
- A truly integrated risk analysis and management process is performed as new technologies and business operations are planned, thus reducing the effort required to address risks identified after implementation.
- Coalfire’s PASS Methodology addresses the 9 Essential Elements.
Next Steps
Connect 1:1 with an ARC-AMPE Expert
