AI Governance
Next-Gen Threat Intelligence Using AWS AgentCore


Turning Threat Intel from Daily Grind to Strategic Advantages
The Overload Problem: Threat Intel as a Daily Grind
Rarely do developers and engineers view staying on top of proper security practices and threat modeling as unimportant. Our days are simply filled with so MANY important things, we’re forced to make tradeoffs. Threat intel is intended to help resolve this problem, and it’s undoubtably one of the most valuable components of an engineer’s toolkit. It gives us critical insight into what emerging threats are within the technical landscape we are tasked with working on at any given time.
And yet with that rapidly evolving technical landscape, and the fact that there are only so many hours in a day to keep up with feeds (let alone digest and act upon ), it’s easy to fall behind as you fight to factor such activities into daily development, testing, and meeting of deadlines. “We are all part of security,” until you prioritize security over shipping that new feature - and then you’re just out of a job.
Here is an example of what a common routine for a security-minded developer or engineer might look like as they try and accomplish this feat of staying informed. Each day they:
- Check vendor security alerts for new vulnerabilities and CVEs
- Check Microsoft Security, Talos, and Unit 42 posts
- Read Krebs on Security, Hacker News and r/NetSec
- Check NSA, CISA, and ENISA
- We thought we’d go through the exercise to see how long it takes - and practiced it.
The table below outlines what that can look like for a lot of organizations and teams:
| Threat Intel Feed | Sites Checked | Effort |
|---|---|---|
| Vendor Vulnerabilities | On average it took 15-20min for each of those. It took a little over 2 hours to iterate through recent vulnerabilities and review them to understand their impact. | |
| Vendor Security Feeds | This took upwards of an hour to read due to new information about nation state actors. | |
| Federal Cybersecurity Resources | Reviewing new and emerging threats disclosed by Governments took over an hour, upwards of 2 hours due to emerging threats. |
As you can see, it can take 4 to 5 hours for someone to iterate through the above sites to review and document relevant data for their own tasks or development team. Imagine doing that daily.
Chances are you aren’t the only one on your team doing it either – there are likely multiple engineers attempting to ingest the same data and taking man-hours from projects. Or maybe this function is done by someone on the security team who then ships daily/weekly spam that few people pay attention to because it lacks actionable steps.
We knew there had to be a better way.
Our First Attempt: Automating the Crawl
As we began developing our own internal security and compliance AI agents and workflows, we decided this would be a rich domain to target.
It doesn’t take a rocket or MIT AI scientist to conclude that injecting some automations and AI could go a long way in helping. In fact, our team had already been aware of and played with basic automations for some time. Yet these solutions were not built for scaling across teams, and they could do little in terms of handling dynamic context or workflows related to risk analysis and more advanced remediation or mitigation recommendations—at least not without launching large-scale integration projects.
We investigated what it might take to grab an existing script from someone on the team and leverage that to help automate. From experience within cloud environments, we started to tackle this challenge by taking a base web crawler that used Sumy or Gensim (Python libraries that handle text summarization) to summarize entries from each of the sites we used.
In order to really scale it, this would require a level of compute and storage to support the workload. Normally, we would build in AWS, which meant spinning up ECS containers, an RDS database, and either an API Gateway or Application Load Balancer. After building this out and validating a proof of concept, we then needed to figure out how to scale it for others—adding containers, handling multi-instance scaling, and ensuring the app could support concurrent usage.
All this was just to get the web crawling running. We still didn’t have a solution for handling dynamic context, performing internal risk analysis, or generating actionable remediation steps that could be integrated into daily stand-ups.
This was our turning point, and where we decided to stop and pivot.
Pivoting to AI Agents
We realized that traditional scripts could only take us so far. Instead of forcing more automation into brittle pipelines, we chose to reframe the problem entirely and pursue an agentic approach.
Rather than leverage traditional summarization algorithms with containerized technologies, we opted to use serverless Generative AI agents to query a predefined list of threat intel feeds. This approach builds on the legacy methodologies of data summarization and brings them a step (really, leaps) further by leveraging large AI models to help ingest, summarize, and contextualize threat intel feeds for querying.
Example queries:
- What critical vulnerabilities were disclosed today, and how can we approach development today to mitigate threats?
- Give me an executive summary of current APT and Nation State threats
- What Microsoft vulnerabilities are being actively exploited?
Instead of spending hours each morning trying to answer the above questions, the AI system frees our time to handle the projects at hand. With the intel digested down into actionable tasks easily injected into our daily development and testing.
Designing the Threat Intel Agent
We began by making a list of 25–30 RSS-based threat intel feeds from various vendors and agencies. This included the NVD from NIST—we planned to grab the last 10 years of CVE data to assist in historic correlation.
We used this list to develop an initial set of hydration data to build a knowledge base to provide recent and near-historic data (90 days, initially).
Initial ingestion script (local):
- Uses list of RSS feeds and NVD API to determine the targets
- Iterates through the feed or API
- Captures each RSS feed entry or CVE entry
- Writes a unique file to S3 for each item captured
We then built infrastructure to support the knowledge base and provide continuous rehydration.
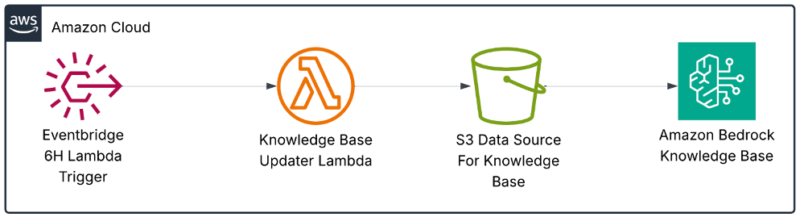
EventBridge-triggered Lambda runs every 6 hours and writes new entries to S3. Bedrock Knowledge Base syncs from that S3 bucket. Hydration scripts populate the initial data, followed by ongoing syncs
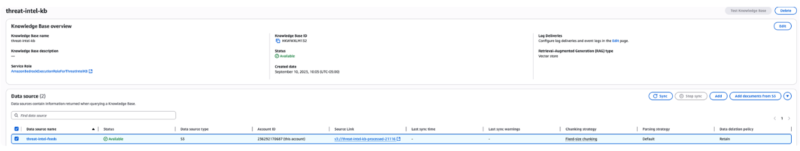
Once the knowledge base was ready, we deployed the agent itself.
Putting It All Together – Threat Intel AI Agent on AWS Bedrock AgentCore
The Threat Intel AI Agent is hosted on AWS Bedrock AgentCore Agent Runtime, providing serverless, scalable infrastructure. We used the Strands Agents SDK in conjunction with AgentCore.
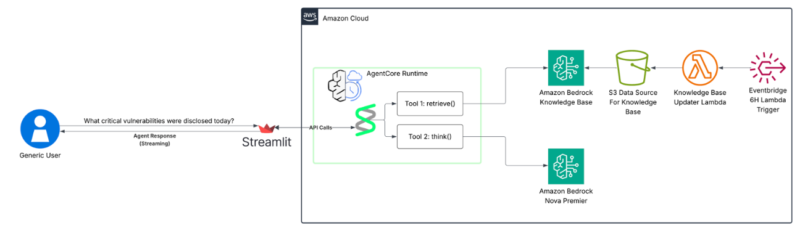
Core tools:
- A retrieve tool that queries and returns results from the Bedrock Knowledge Base
- A think tool that queries a configured Bedrock model to trigger reasoning
Deployment to AgentCore Agent Runtime was straightforward – two commands.
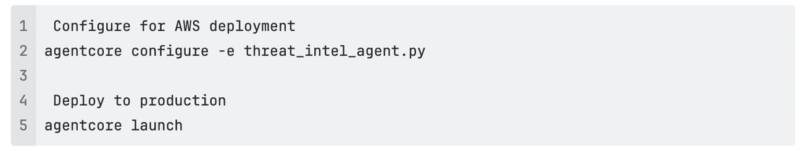
Seven minutes later, we had a production AI Agent. AgentCore handled:
- Container building and optimization
- Serverless runtime deployment
- Auto-scaling configuration
- Security and IAM setup
- Monitoring and logging
Our manual process of threat intelligence data gathering was now a production service that could handle thousands of requests.
Real-World Usage
Once deployed, the agent began integrating naturally into our daily developer and security workflows.
DevSecOps Check:
agentcore invoke '{"prompt": "What vulnerabilities should I be aware of today as I develop a new app in Python3.11, Nginx and PostgreSQL?"}'
Executive Reporting:
agentcore invoke '{"prompt": "What ATP and Nation State threats this month require board visibility?"}'
The agent filters through thousands of security advisories and surfaces only what matters to our environment.
The Impact: From Hours to Minutes
We can honestly say this changed everything about how we approach threat intel—particularly in how to close the gap between the intel we get and making it more timely and actionable during in our daily sprints.
Remember that 4–5-hour marathon from earlier? That’s ancient history now. Instead, we start our mornings with a simple query to the agent before standups and have already started talking about developing an MCP integration with our sprint ticketing process to be even more proactive and streamlined.
Our DevSecOps stand-ups evolved. Instead of scrambling to brief the team on overnight emergencies, we now use the agent’s analysis to drive proactive security discussions. We query it before deploying new services, catching potential issues during design rather than in production. It’s become as natural as running unit tests.
Monthly leadership briefings have also transformed. We went from cobbling together threat reports at the last minute to presenting comprehensive landscape analysis with actual strategic value (our excessive technical jargon is translated into business-level impact statements).
All those hours we used to spend parsing through vendor alerts and government advisories are now spent engineering solutions. The agent handles the information overload that once crushed us.
Conclusion: Turning Overload into Insight
Threat intelligence no longer has to be a daily grind or a bottleneck. By reframing it as an agentic workflow, we turned an overwhelming flood of data into timely, contextual insight. Our engineers focus on building resilient systems instead of parsing endless feeds.
This same pattern – automated intake, contextual reasoning, and actionable output—can be applied far beyond threat intel. If you’re still drowning in data, it might be time to let an agent take the first watch.
Find this work interesting?
Coalfire’s AI Security and Trust Engineering works on these types of problems daily, and provides a number of services related to securing AI agents and agentic workflows, and building security and compliance agents for our customers and partners.
Read more about Coalfire’s point of view on GenAI, AI agents, and Agentic AI here.